In an increasingly digital world, where information flows freely and transactions occur at the click of a button, the need for robust online security has never been more critical. Organizations and individuals alike must adopt measures that safeguard sensitive data, prevent unauthorized access, and ensure a seamless user experience. One of the cornerstones of modern security infrastructure is Single Sign-On (SSO) and authentication mechanisms. In this blog post, we’ll delve into the world of SSO and authentication, exploring their significance, benefits, and best practices.
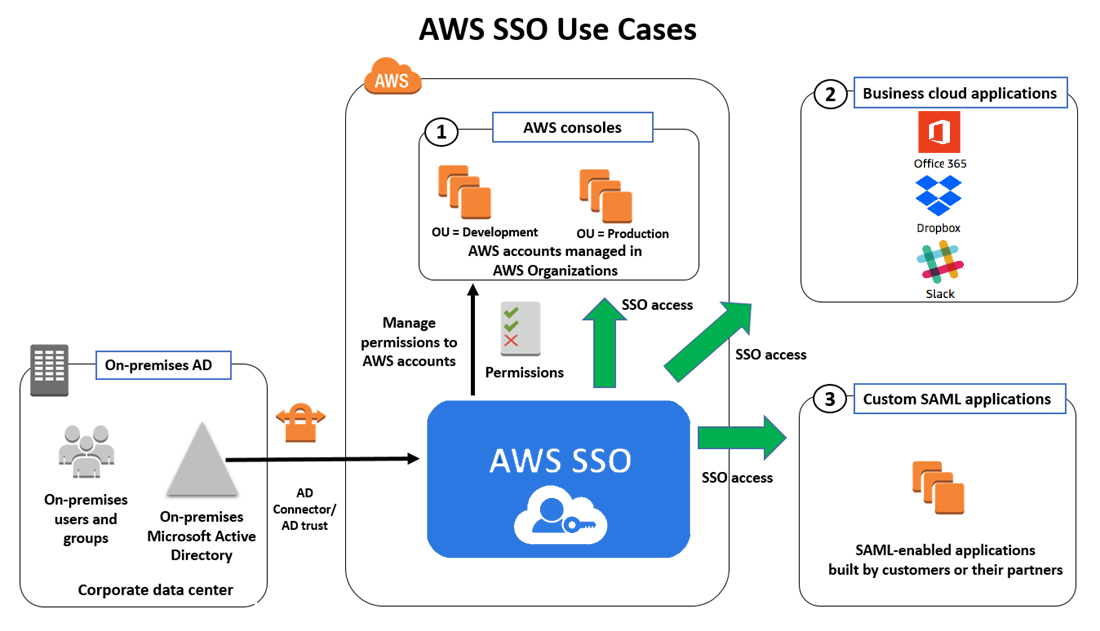
Understanding Single Sign-On (SSO)
Single Sign-On (SSO) is a authentication process that allows users to access multiple applications and services with a single set of credentials. Traditionally, users had to remember distinct usernames and passwords for each application they used, resulting in security risks and user frustration. SSO addresses this challenge by enabling users to authenticate once and gain access to various interconnected systems seamlessly.
Key Benefits of SSO:
- Enhanced Security:
- SSO reduces the number of passwords users need to remember, which can lead to stronger, unique passwords. It also enables centralized management of user access, making it easier to enforce security policies and revoke access if needed.
- Streamlined User Experience:
- With SSO, users can access multiple applications without the need to repeatedly enter credentials, leading to a smoother and more user-friendly experience.
- Reduced Password Fatigue:
- Users no longer have to manage an overwhelming number of passwords, reducing the risk of password-related issues and increasing overall productivity.
- Centralized Access Control:
- IT administrators can control user access from a central location, making it simpler to monitor and manage user privileges across different applications.
Authentication: The First Line of Defense
Authentication is the process of verifying the identity of a user, device, or system attempting to access a digital resource. It is the fundamental building block of online security and plays a crucial role in protecting sensitive information from unauthorized access.
Types of Authentication Factors:
- Knowledge Factor:
- This involves something the user knows, such as a password, PIN, or answer to a security question.
- Possession Factor:
- This involves something the user possesses, like a physical token, smartphone, or smart card.
- Inherence Factor:
- This is a biometric factor, such as fingerprint, facial recognition, or voice recognition.
Best Practices for Secure Authentication:
- Multi-Factor Authentication (MFA):
- Implementing MFA adds an extra layer of security by requiring users to provide multiple forms of authentication before gaining access.
- Regularly Update Passwords:
- Encourage users to update their passwords regularly and avoid using common or easily guessable passwords.
- Use Adaptive Authentication:
- Adaptive authentication systems analyze user behavior and context to determine the level of authentication required, enhancing security while maintaining user convenience.
- Implement Strong Encryption:
- Ensure that data transmission and storage are encrypted using industry-standard encryption protocols.
- Continuous Monitoring:
- Regularly monitor and audit authentication logs to detect and respond to suspicious activities promptly.
Conclusion: A Unified Approach to Security
In the digital landscape, where data breaches and cyber threats are on the rise, organizations and individuals must adopt a unified approach to security that prioritizes both user experience and data protection. Single Sign-On (SSO) and authentication mechanisms stand as pillars of this approach, fortifying online security, and granting users the confidence to navigate the digital realm securely. By embracing SSO and following best practices for authentication, we can create a safer and more seamless online experience for everyone.
If you are in need of help configuring or setting up any of these services please feel free to reach out to us, it’s what we do all day every day. Contact Us
